Today we decided to release another of our tools.
This tool was developed when we are investigating some "Phishing" attacks which the malware writers made victims to believe that the Chrome extension was legit and have lots of features. Thus, we wanted something which allows us to download quite a number of Chrome Extensions and go through each and one of them to verify that it's legit and not with malicious intent.
We hope that this tool will be useful to some of you if not all of you.
The tool could be found here.
CRX Downloader
Have Phun
doraemon.sk8ers
Nops"R"Us - Home to Doraemon.Sk8ers
Friday, March 7, 2014
Decrypting Tools for TP-Link and Cisco Type 7
2 of our members, 0x4a61636f62 & Johnny Deep, decided to release some tools after reading the article by Piotr Bania on how easy it was to retrieve the password to our TP-LINK routers and few other router devices.
We decided to dive deeper and create this tool just in case you lost the password to your TP-Link router as well.
Another tool which we decided to release today is a tool which we have previously developed when we lost the password to our old Cisco routers but all we got was an "encrypted" password.
We hope to release more tools in the near future and hope everyone will learn something from the tools.
The tools could be found here:
CiscoType7Decoder
ROM0_Decoder
Have Phun
doraemon.sk8ers
We decided to dive deeper and create this tool just in case you lost the password to your TP-Link router as well.
Another tool which we decided to release today is a tool which we have previously developed when we lost the password to our old Cisco routers but all we got was an "encrypted" password.
We hope to release more tools in the near future and hope everyone will learn something from the tools.
The tools could be found here:
CiscoType7Decoder
ROM0_Decoder
Have Phun
doraemon.sk8ers
Tuesday, January 28, 2014
Nullcon HackIM 2014 :: Reverse 1
For this particular challenge, we were given a file (which i've re-uploaded here) and the following clues.
"Find the flag hidden not so deep inside."
After opening up the .zip file, there is an easy.exe file within.
My initials gut feel is to simply step-debug this .exe file but realise that it's not doing anything interesting so i loaded it up into IDA Pro and found this interesting function that is never being called.
Let's extract out this function and form it back to C code like this here.
We should have something like the file that i've attached here.
If you compile and run the program, you will get the key.
6a589746613a5f670583086124a8305a_AND_MOOOO
Have Phun
0x4a61636f62
"Find the flag hidden not so deep inside."
After opening up the .zip file, there is an easy.exe file within.
My initials gut feel is to simply step-debug this .exe file but realise that it's not doing anything interesting so i loaded it up into IDA Pro and found this interesting function that is never being called.
Let's extract out this function and form it back to C code like this here.
#include <stdio.h>#include <stdlib.h>#include <string.h>int main(int argc, char* argv[]){int v0 = strlen(")T(+,*'))$&T(Y)*#(+&#+)$%'T+&#(T");int v3 = v0 + 32;char *result = (char *)malloc(v0 + 32);char wtf[] = {")T(+,*'))$&T(Y)*#(+&#+)$%'T+&#(T"};int i;if ( result ){int v2 = 0;memset(result, 0, v3);for ( i = 0; i<strlen(")T(+,*'))$&T(Y)*#(+&#+)$%'T+&#(T"); ++i )*(result + i) = wtf[i] + 13;*(result + i) = 95;v2 = i + 1;*(result + v2++) = 65;*(result + v2++) = 78;*(result + v2++) = 68;*(result + v2++) = 95;*(result + v2++) = 77;*(result + v2++) = 79;*(result + v2++) = 79;*(result + v2) = 79;*(result + v2 + 1) = 79;}printf("%s", result);return 0;}
We should have something like the file that i've attached here.
If you compile and run the program, you will get the key.
6a589746613a5f670583086124a8305a_AND_MOOOO
Have Phun
0x4a61636f62
Monday, January 27, 2014
Nullcon HackIM 2014 :: Misc 3
We were given only the following clues
"Find the flag hidden not so deep inside."
and a file which i've re-uploaded here
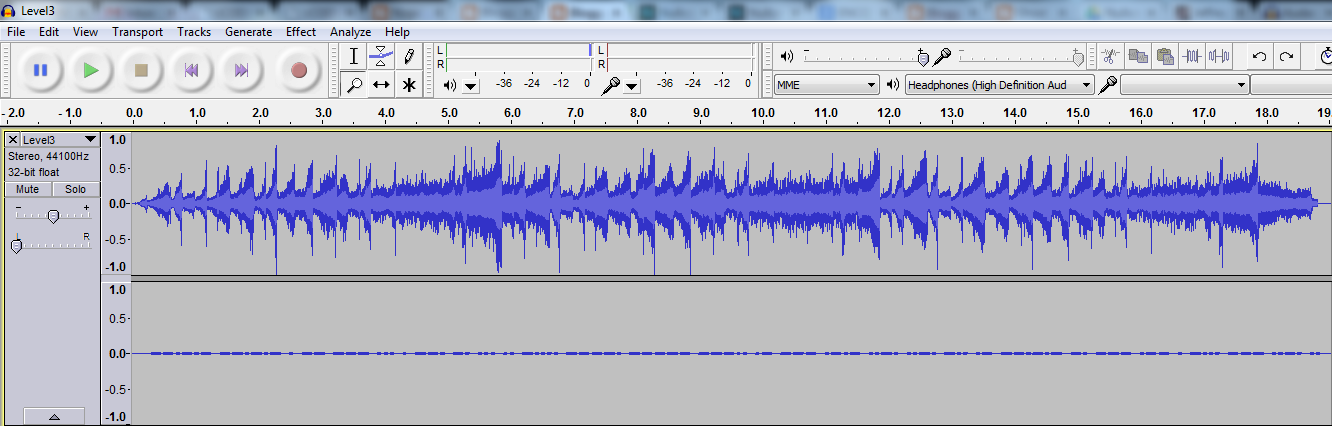
For music files, usually i will use Audacity to see whether there are hidden clues within.
From the above screenshot, we can see there seems to be 2 audio tracks within 1 .mp3 file.
The 2nd audio track when you zoom in seems like "-" & ".".
Could it be morse code?
Let's extract out and try decoding it.
After extraction of the morse code, it will look like this.
We were given back ??EMOSEGNSI6908AO?FFDA?NOWEBOFI
Doesn't seems like it.
Then i listened to the other track and the music sounded strange as if it's music played backwards.
So i used one of the features in Audacity to reverse the .mp3 file and track 1 sounds better now.
So probably the morse code from track 2 should be read from back to front too.
After reversing the morse code, we got back
ILOVEGOA?NULLCON2014ISAWESOME??
So we got a character that are not properly translated
-.-.--
But checking with Wiki, that is equal to !
Therefore, the final answer to this challenge is the following.
ILOVEGOA!NULLCON2014ISAWESOME!!
cheers
0x4a61636f62
"Find the flag hidden not so deep inside."
and a file which i've re-uploaded here
For music files, usually i will use Audacity to see whether there are hidden clues within.
From the above screenshot, we can see there seems to be 2 audio tracks within 1 .mp3 file.
The 2nd audio track when you zoom in seems like "-" & ".".
Could it be morse code?
Let's extract out and try decoding it.
After extraction of the morse code, it will look like this.
However after using the Morse Code translator from http://morsecode.scphillips.com/jtranslator.html--.-.- --.-.- . -- --- ... . --. -. ..... -.... ----. ----- ---.. .- --- .-.- ..-. ..-.-.. .- --.-.- -. --- .-- . -... --- ..-. ..
We were given back ??EMOSEGNSI6908AO?FFDA?NOWEBOFI
Doesn't seems like it.
Then i listened to the other track and the music sounded strange as if it's music played backwards.
So i used one of the features in Audacity to reverse the .mp3 file and track 1 sounds better now.
So probably the morse code from track 2 should be read from back to front too.
After reversing the morse code, we got back
After using the morse code to text translator, we got back the following.--.-.- --.-.- . -- --- ... . --. -. ..... -.... ----. ----- ---.. .- --- .-.- ..-. ..-.-.. .- --.-.- -. --- .-- . -... --- ..-. ..
ILOVEGOA?NULLCON2014ISAWESOME??
So we got a character that are not properly translated
-.-.--
But checking with Wiki, that is equal to !
Therefore, the final answer to this challenge is the following.
ILOVEGOA!NULLCON2014ISAWESOME!!
cheers
0x4a61636f62
Nullcon HackIM 2014 :: Misc 1
The clues given to us are
"Sam has parked his car in front of a store. Find the name of the store."
and we were also given a .pcap file I've uploaded a copy of the .pcap file here First thing i did was load the .pcap file into Wireshark and check whether there are any file objects and i saw just 1 image.
As the question was "Find the name of the store" So i extracted the image and try to see whether there are any GPS information in the file. So i use http://regex.info/exif.cgi to check for GPS information. Surprisingly there is indeed GPS information and Google Maps as shown below
Making use of Google Maps's Street View, i found this.
Ok and the answer to this challenge is..... "Wells Fargo" :D
cheers
0x4a61636f62
"Sam has parked his car in front of a store. Find the name of the store."
and we were also given a .pcap file I've uploaded a copy of the .pcap file here First thing i did was load the .pcap file into Wireshark and check whether there are any file objects and i saw just 1 image.
As the question was "Find the name of the store" So i extracted the image and try to see whether there are any GPS information in the file. So i use http://regex.info/exif.cgi to check for GPS information. Surprisingly there is indeed GPS information and Google Maps as shown below
Making use of Google Maps's Street View, i found this.
Ok and the answer to this challenge is..... "Wells Fargo" :D
cheers
0x4a61636f62
Nullcon HackIM 2014 :: Programming 1
For this particular challenge, we were given with the following clues.
Based on the clues, i guess we are supposed to write a Client application to connect to the server, 23.23.190.204:2002, and passed in the correct parameters.
After playing around with the server, we need to send in 20 words that are commonly used in SPAM mails.
Thus, i developed this simple script.
https://gist.github.com/anonymous/8661737
Using the Python script, we will eventually get the flag.
The flag is "f94b50f9972398811e7d76928d2e87d4"
cheers
0x4a61636f62
One evening Holmes visits Watson looking thinner and paler than usual and with the knuckles of one hand burst and bleeding. Holmes asks Watson if he has ever heard of Professor Moriarty and Watson replies that he has not. Holmes explains that Professor Moriarty is the central organizational force of a large portion of criminal activity in the city of London. Holmes also describes Moriarty as his intellectual equal and the Napoleon of Crime.
To find out the extent of Moriaty’s criminal network, Holmes decided the break the encrypted communication happening in Moriaty’s criminal network. To make the communication secure and at the same time easy, Moriaty devised an algorithm to generate passwords (consisting only lowercase alphabets) that are easy to remember.
Holmes has got access to one of the communication, Holmes challenge is to gather passwords as many as possible.
Holmes requires you help!!!
Connect to 23.23.190.204:2002
Based on the clues, i guess we are supposed to write a Client application to connect to the server, 23.23.190.204:2002, and passed in the correct parameters.
After playing around with the server, we need to send in 20 words that are commonly used in SPAM mails.
Thus, i developed this simple script.
https://gist.github.com/anonymous/8661737
Using the Python script, we will eventually get the flag.
The flag is "f94b50f9972398811e7d76928d2e87d4"
cheers
0x4a61636f62
Nullcon HackIM 2014 :: Trivia 1-5
Trivia 1 :
This esoteric programming language uses AWSUM THX and O NOES as error handling.
Searching for "AWSUM THX" and the top entry is en.wikipedia.org/wiki/LOLCODE
So the answer is "LOLCODE"
Trivia 2 :
What software is used to hack into ENCOM's computer system?
If you had watched the movie "Tron", you might remember names like MCP but the actual software used to hack into ENCOM is "CLU"
http://tron.wikia.com/wiki/Clu
Trivia 3 :
Outcome of Stealth Project to make coffee.
"Java" :D
Trivia 4 :
Successor of the DEAD persistent object format
DEAD persistent object format basically refers to Java Class file. It has been eventually replaced by RMI. :D
Trivia 5 :
Oheebhtuf O6700 "havavgvnyvmrq" zrzbel (48-ovg)
If you do a quick google for "havavgvnyvmrq", the top hit might be http://easyciphers.com/uninitialized
Looking at the page, you will realised it's a Caesar Cipher shift or simply ROT13.
You will get "Burroughs B6700 "uninitialized" memory (48-bit)"
Using the new found clues, "Burroughs B6700 "uninitialized" memory (48-bit)"
You will find the following page.
http://www.retrocomputingtasmania.com/home/projects/burroughs-b6700-mainframe/tidbits
The "uninitialised" memory is actually "0xBADBADBADBAD" which is the answer. :D
Have Phun
0x4a61636f62
This esoteric programming language uses AWSUM THX and O NOES as error handling.
Searching for "AWSUM THX" and the top entry is en.wikipedia.org/wiki/LOLCODE
So the answer is "LOLCODE"
Trivia 2 :
What software is used to hack into ENCOM's computer system?
If you had watched the movie "Tron", you might remember names like MCP but the actual software used to hack into ENCOM is "CLU"
http://tron.wikia.com/wiki/Clu
Trivia 3 :
Outcome of Stealth Project to make coffee.
"Java" :D
Trivia 4 :
Successor of the DEAD persistent object format
DEAD persistent object format basically refers to Java Class file. It has been eventually replaced by RMI. :D
Trivia 5 :
Oheebhtuf O6700 "havavgvnyvmrq" zrzbel (48-ovg)
If you do a quick google for "havavgvnyvmrq", the top hit might be http://easyciphers.com/uninitialized
Looking at the page, you will realised it's a Caesar Cipher shift or simply ROT13.
You will get "Burroughs B6700 "uninitialized" memory (48-bit)"
Using the new found clues, "Burroughs B6700 "uninitialized" memory (48-bit)"
You will find the following page.
http://www.retrocomputingtasmania.com/home/projects/burroughs-b6700-mainframe/tidbits
The "uninitialised" memory is actually "0xBADBADBADBAD" which is the answer. :D
Have Phun
0x4a61636f62
Sunday, January 19, 2014
Ghost in the Shellcode 2014 :: Pwn Adventure 2 :: Boaring Music (50 points)
For this challenge, a key is required to be obtain from the given file.
The file (I re-hosted the file on MediaFire) can either be obtain from the website
or from the game folder of pwnadventure2_Data.
The next paragraph explain the steps need to be taken if file is obtain from the website. Skip the next paragraph if its obtain from the game folder.
If the file is obtain from the website, the file extension will need to be identify. The file is identified to be an .xz file using TRid online. Opening the .xz file with 7zip, it contain another file without a file extension. After identifying the file, it is the same .ogg file that can be obtain from the game folder.
The .ogg audio file can be played and analyse using audacity. After listening to the audio file, I notice that there is a constant beeping sound in the music that have resemblance to the beeping of Morse code.
Waveform of a beep:
Waveform of a dash:
The first beep starts around 18.10s .
After listening to the entire audio file, the Morse code is obtained:
.- ... - .- .-. .. ... -... --- .- .-. -.
Converting the Morse code...
ASTARISBOARN
entering the key and 50 points =D
whit3sn0w^_^
The file (I re-hosted the file on MediaFire) can either be obtain from the website
or from the game folder of pwnadventure2_Data.
The next paragraph explain the steps need to be taken if file is obtain from the website. Skip the next paragraph if its obtain from the game folder.
If the file is obtain from the website, the file extension will need to be identify. The file is identified to be an .xz file using TRid online. Opening the .xz file with 7zip, it contain another file without a file extension. After identifying the file, it is the same .ogg file that can be obtain from the game folder.
The .ogg audio file can be played and analyse using audacity. After listening to the audio file, I notice that there is a constant beeping sound in the music that have resemblance to the beeping of Morse code.
Waveform of a beep:
Waveform of a dash:
The first beep starts around 18.10s .
After listening to the entire audio file, the Morse code is obtained:
.- ... - .- .-. .. ... -... --- .- .-. -.
Converting the Morse code...
ASTARISBOARN
entering the key and 50 points =D
whit3sn0w^_^
Friday, October 25, 2013
hack.lu 2013 CTF :: Reversing: RoboAuth (150 points)
The challenge:
Oh boy, those crazy robots can't catch a break! Now they're even stealing our liquid gold from one of our beer tents! And on top of that they lock it behind some authentication system. Quick! Access it before they consume all of our precious beverage!
Flag: password1_password2
An executable file is uploaded it to Wikisend and can be downloaded from here. The image below show how it looks like when it is executed.
The objective of this challenge is to reverse the executable file to obtain the passwords which is the flag.
First, we open up the executable with IDA pro to look for useful information. In the string tab, a particularly interesting string is spotted.
Go to the code that uses this string...
From the image above, it is observed that the executable call scanf then compare the input with a value to decide the location to jump.
Open the executable with ollydbg and set breakpoints at the two mov operation. Debug the executable and we will see the value in the EAX that might be the first password.
Enter and yes ! It is the first password !
One down, one to go.
Go back to IDA pro, it is observed that executable is moving some values into the memory...
and there is a subroutine that seems to be decoding the value that moved into the memory.
Go to ollydbg and set breakpoint before and after the decoding subroutine.
Before decoding:
After decoding:
We notice that a particular string that is decoded but is not used anywhere yet. So we set a hardware breakpoint to see where the string is used. (Do note that we need to go to the debugging option to ignore INT3)
Upon entering the second password, we will something like this.
Analysing the code, we notice that it is comparing the second password input character by character with the interesting string (u1nnf2lg) XOR with 2.
XORing u1nnf2lg with 2 we will get w3lld0ne.
Entering both passwords and ..
The flag for this challenge: r0b0RUlez!_w3lld0ne
whit3sn0w ^^
Oh boy, those crazy robots can't catch a break! Now they're even stealing our liquid gold from one of our beer tents! And on top of that they lock it behind some authentication system. Quick! Access it before they consume all of our precious beverage!
Flag: password1_password2
An executable file is uploaded it to Wikisend and can be downloaded from here. The image below show how it looks like when it is executed.
The objective of this challenge is to reverse the executable file to obtain the passwords which is the flag.
First, we open up the executable with IDA pro to look for useful information. In the string tab, a particularly interesting string is spotted.
Go to the code that uses this string...
From the image above, it is observed that the executable call scanf then compare the input with a value to decide the location to jump.
Open the executable with ollydbg and set breakpoints at the two mov operation. Debug the executable and we will see the value in the EAX that might be the first password.
Enter and yes ! It is the first password !
One down, one to go.
Go back to IDA pro, it is observed that executable is moving some values into the memory...
and there is a subroutine that seems to be decoding the value that moved into the memory.
Go to ollydbg and set breakpoint before and after the decoding subroutine.
Before decoding:
We notice that a particular string that is decoded but is not used anywhere yet. So we set a hardware breakpoint to see where the string is used. (Do note that we need to go to the debugging option to ignore INT3)
Upon entering the second password, we will something like this.
Analysing the code, we notice that it is comparing the second password input character by character with the interesting string (u1nnf2lg) XOR with 2.
XORing u1nnf2lg with 2 we will get w3lld0ne.
Entering both passwords and ..
The flag for this challenge: r0b0RUlez!_w3lld0ne
whit3sn0w ^^
Monday, September 23, 2013
CSAW CTF 2013 :: RE: Impossible (500 points)
We are given a nds rom for this puzzle.
Tools used:
Tools used:
- CheatEngine (1 of my favorite old tool to hack a game)
- OllyDbg
- NO$GBA for my nds emulator
Lets keep this puzzle simple. It is mentioned that the boss hp is 9000++ which means there is probably no way to kill him unless we cheat. The following is a screenshot of the impossible boss...
Lets fire up CheatEngine... The following is a screenshot of this tool...
What this tool does is that it allows us to search for values in memory... which eventually narrow down where is the boss hp memory address. Once we know where is the address, we can easily modify it to 0 =).
We used the scan type option in the tool to narrow down addresses. Below are the steps on how we did it.
- Start Game
- find unknown initial value
- Reset Game
- shoot target
- find decreased value
- Reset Game
- find increased value
- repeat from step 3
As you can see from the above screenshot, we have narrowed down the possible hp memory address to this few addresses. Seems like address 03BC2264 is a potential candidate. Wait a minute didn't the question say that the boss hp is more than 9000... seems like it is more than 900,000! We changed the value @ the memory address to 0. Reset the game and shoot 1 round at the boss! We won the game!
But it seems like the key is incomplete/wrong... Lets fire up ollydbg to see what we can find out... since we got the memory address of the boss hp, the key should be somewhere around that memory region... true enough we found it above the boss hp!
The key is ou6UbzM8fgEjZ????cXKVN?
If you recall.... earlier we use cheatengine tool to actively fix the value @ 03BC2264 (DWORD) to be 0 and it happen that the key we wanted is overwriting/overlapping this address as well. To resolve the 0 bytes issue, disable actively fixing the value @ 03BC2264 after the game had initialized (when the boss appears on the screen). You should get the full key once the boss is dead after shooting it once.
The key is ou6UbzM8fgEjZQcRrcXKVN
Always lazing
NoirD3vil
Subscribe to:
Posts (Atom)