Step 1: Load the pcap file with Wireshark.
Step 2: Go to packet num 767. This is a packet containing a HTTP GET request that reveals a wget command was executed to download the payload file (rootkit.zip). The file can be saved to a working directory by looking up Wireshark HTTP object list. In Wireshark, go to File > Export > Objects > HTTP, to bring up the HTTP object list. Any attempt to unzip the zipped file (to view flag.txt) will fail as it is protected with a password.
Step 3: Go to packet num 8. Right click on the packet, select "Follow UDP Stream", "ASCII", and save the entire conversation as an ASCII file. View the saved file with your preferred text editor. The password lies between line 593 and line 609.
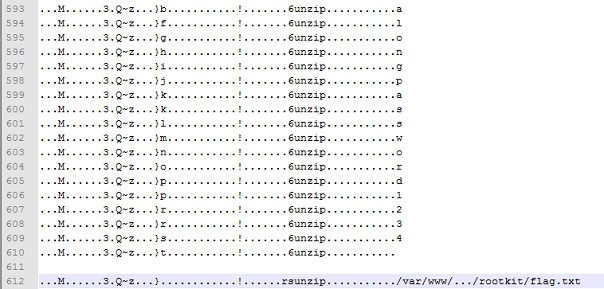
Step 4: Use the extracted password to retrieve flag.txt from rootkit.zip. The flag for this challenge lies within flag.txt. 100 points in the bag!! Yay!!!
Flag: ebCTF{b78dc61ce895a3856f3520e41c07b1be}
Cheers,
Braeburn Ladny
No comments:
Post a Comment