Oh boy, those crazy robots can't catch a break! Now they're even stealing our liquid gold from one of our beer tents! And on top of that they lock it behind some authentication system. Quick! Access it before they consume all of our precious beverage!
Flag: password1_password2
An executable file is uploaded it to Wikisend and can be downloaded from here. The image below show how it looks like when it is executed.
The objective of this challenge is to reverse the executable file to obtain the passwords which is the flag.
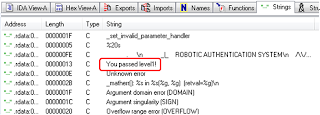
First, we open up the executable with IDA pro to look for useful information. In the string tab, a particularly interesting string is spotted.
Go to the code that uses this string...
From the image above, it is observed that the executable call scanf then compare the input with a value to decide the location to jump.
Open the executable with ollydbg and set breakpoints at the two mov operation. Debug the executable and we will see the value in the EAX that might be the first password.
Enter and yes ! It is the first password !
One down, one to go.
Go back to IDA pro, it is observed that executable is moving some values into the memory...
and there is a subroutine that seems to be decoding the value that moved into the memory.
Go to ollydbg and set breakpoint before and after the decoding subroutine.
Before decoding:
We notice that a particular string that is decoded but is not used anywhere yet. So we set a hardware breakpoint to see where the string is used. (Do note that we need to go to the debugging option to ignore INT3)
Upon entering the second password, we will something like this.
Analysing the code, we notice that it is comparing the second password input character by character with the interesting string (u1nnf2lg) XOR with 2.
XORing u1nnf2lg with 2 we will get w3lld0ne.
Entering both passwords and ..
The flag for this challenge: r0b0RUlez!_w3lld0ne
whit3sn0w ^^