Solution for www.net-force.nl : Level 404 Hiding in a pipe
This is the link to the original challenge: http://www.net-force.nl/challenge/level404/portal.php
Quest:
Hack this 'portal' to find the password :-)
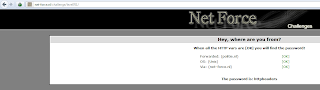
This puzzle is an easy one. The hint given to us is hiding in a pipe. The portal provide us with 3 forms which allow us to DES crypt, finger a user and ping itself. As shown below...
Now we all know that ping is a standard command... could it be that the server take in the text box value and pass it off as a command? let us try to modify ping netforce.nl to ls instead... ah... somehow it failed... there must be some sort of filtering... but wait what will happen if we were to pipe another command behind this ping? Let us try "ping netforce.nl | ls" in the textbox...
wow... we got something here.... whats in info.txt?
try this link: http://www.net-force.nl/challenge/level404/info.txt
it states... Nice one, you have finished the first part...proceed
=( continue to part 2... there is a protected folder... question is how do we get to the folder when an authentication is required...
ah... remember in the portal.php? there is a finger user textbox with a default username in it: "BasTijs". But no password is given... let us just try the username with no password... bingo we got in! It shows us the files in the protected folder and solution.php is the password to this puzzle.
Password: pijpme!
it states... Nice one, you have finished the first part...proceed
=( continue to part 2... there is a protected folder... question is how do we get to the folder when an authentication is required...
ah... remember in the portal.php? there is a finger user textbox with a default username in it: "BasTijs". But no password is given... let us just try the username with no password... bingo we got in! It shows us the files in the protected folder and solution.php is the password to this puzzle.
Password: pijpme!
Cheers
3lucidat0r